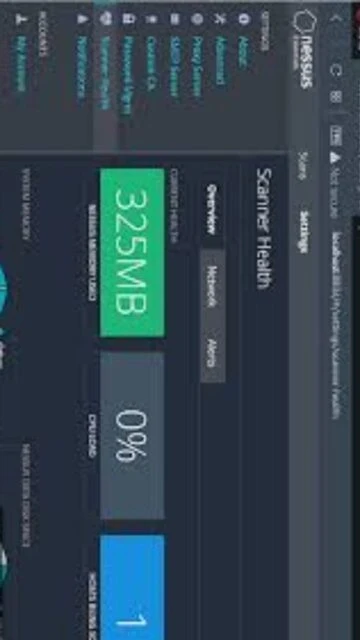
Nessus Professional is the gold standard vulnerability assessment solution trusted by security practitioners, enterprises, and government agencies worldwide. With the industry’s most comprehensive plugin library containing 293,000+ vulnerability definitions and over 100 new plugins released weekly, Nessus delivers unmatched vulnerability coverage and accuracy. This definitive guide covers installation procedures, feature utilization, platform deployment strategies, integrations, competitive positioning, and optimization techniques to maximize vulnerability assessment effectiveness with Nessus Professional.
How to Install Nessus Professional
Nessus Professional installation is straightforward and can be completed in minutes. The installer bundles all necessary dependencies and automatically configures database services. Installation varies slightly across platforms but follows consistent procedures ensuring rapid deployment and minimal configuration overhead.
- Download from Official Source – Visit tenable.com/products/nessus and download the installer for your platform (Windows .exe, macOS .dmg, or Linux .run file). Registration with Tenable requires email verification for license activation.
- Execute Installer – Run the downloaded installer package. On Windows, accept User Account Control prompts. Installation automatically starts the Nessus service and configures system integrations for immediate use.
- Register License Activation Code – Obtain activation code from Tenable portal after purchase. Access https://localhost:8834 in browser and enter activation code through web interface to register your Professional license.
- Complete Initial Setup – Create administrator account, configure network settings, and download initial plugin package. First plugin compilation typically requires 15-30 minutes; Nessus automatically updates plugins weekly afterward.
Who Should Use Nessus Professional
Nessus Professional serves security professionals requiring comprehensive vulnerability assessment without enterprise management overhead. Individual consultants, small security teams, and organizations prioritizing rapid vulnerability identification benefit from Nessus’s intuitive interface, extensive automation, and compliance-focused features without the complexity of enterprise deployments.
- Independent Security Consultants – Consultants conducting client vulnerability assessments require Nessus’s portability, comprehensive reporting, and ability to scan diverse client networks without complex infrastructure requirements.
- Small to Mid-Size Security Teams – Teams managing vulnerability assessment across 10-100 systems benefit from Nessus’s ease-of-use, automated compliance auditing, and pre-built scanning policies suitable for diverse IT environments.
- Educational Institutions – Universities and training organizations use Nessus to teach vulnerability assessment fundamentals; free Nessus Essentials licenses available for students and educators.
- NOT ideal for – Large enterprises managing thousands of assets should evaluate Tenable.io or Tenable.sc for centralized management; users requiring vulnerability assessment without exploitation should consider Nessus Essentials (free).
Nessus Professional Platform Compatibility
Nessus Professional deploys across diverse platforms including traditional servers, Linux distributions, macOS workstations, and even Raspberry Pi devices. Platform consistency ensures identical scanning capabilities regardless of deployment location, enabling flexible vulnerability assessment across heterogeneous environments and remote operational scenarios.
| Platform |
Min. Version |
Unique Features |
Limitations |
| Windows |
Windows 10 (64-bit) or Windows Server 2012 R2+ |
Windows Service auto-start, Windows credentials integration, native Windows Defender compatibility, FIPS compliance |
Removed 32-bit support in version 10.11; requires Visual C++ Redistributable |
| macOS |
macOS 11.0+ (Intel/Apple Silicon) |
Native ARM64 support, system keychain integration, background service operation, Homebrew package management |
Some advanced plugins limited; filesystem integration varies by macOS version |
| Linux |
Ubuntu 20.04, Debian 10, CentOS 8, RHEL 8+ |
Systemd service integration, Docker container deployment, system package manager updates, support for 50+ distributions |
Requires Linux knowledge for advanced configuration; headless operation only |
| Raspberry Pi |
Raspberry Pi OS (32/64-bit), latest updates |
Lightweight scanning for IoT networks, remote office deployments, low-power vulnerability assessment |
Performance limited; suitable for small networks only; not recommended for 50+ host scans |
Nessus Professional Integrations & Plugins
Nessus Professional integrates with enterprise security infrastructure, vulnerability management platforms, and ticketing systems. Strategic integrations enable automated vulnerability workflows, centralized reporting, and seamless data sharing across security operations teams and external compliance partners.
- Tenable.io Integration – Nessus scanners report findings to cloud-based Tenable.io for centralized analytics, multi-scanner management, and advanced correlation across distributed scanning infrastructure.
- Tenable.sc/Security Center – On-premise deployments integrate with Tenable.sc for policy management, historical trending, advanced reporting, and centralized credential management across multiple scanners.
- SIEM Integration – Nessus exports scan results to Splunk, ELK, ArcSight, and other SIEM platforms through syslog, API, or direct connectors for threat correlation and incident response.
- Ticketing System Connectors – Integration with ServiceNow, Jira, and other ticketing platforms enables automated remediation tracking, vulnerability assignment, and SLA compliance monitoring.
Best Alternatives to Nessus Professional
While Nessus leads vulnerability assessment, alternative scanners excel in specific scenarios. Organizations prioritizing cost-reduction, specialized scanning, or advanced exploitation should evaluate alternatives aligned with assessment requirements and operational constraints.
- OpenVAS – Best for cost-conscious organizations, OpenVAS provides free vulnerability scanning with comparable coverage to older Nessus versions; suitable for resource-constrained environments and open-source deployments.
- Qualys VMDR – Best for enterprise asset management, Qualys cloud-based vulnerability detection excels in asset discovery and continuous monitoring; requires cloud connectivity and subscription commitment.
- Rapid7 InsightVM – Best for consolidated risk assessment, InsightVM combines vulnerability scanning with real-time threat intelligence for advanced risk prioritization suitable for enterprises managing thousands of assets.
- Acunetix Web Scanner – Best for web application vulnerability scanning, Acunetix specializes in HTTP-based vulnerabilities with superior JavaScript analysis and automated exploitation detection.
Nessus Professional vs Top Competitors
Nessus Professional maintains competitive advantages in plugin coverage, ease-of-use, and cost-effectiveness when compared to specialized competitors. While Nessus excels in comprehensive vulnerability assessment, competing solutions offer superior focus on specific domains like cloud infrastructure, web applications, or advanced asset management.
| Feature |
Nessus Professional |
OpenVAS |
Rapid7 InsightVM |
| Pricing |
$2,990/year per user |
Free (open-source) |
$3,000-$50,000+ annually (cloud-based) |
| Key Strength |
Largest plugin library (293,000+); ease-of-use; compliance auditing |
Cost-free; open-source flexibility; community support |
Real-time threat intelligence; asset discovery; risk prioritization |
| Target Users |
Individual consultants; small-to-mid security teams; educators |
Cost-constrained organizations; academic institutions; open-source advocates |
Enterprise security operations; large-scale asset management; Fortune 500 companies |
| Unique Feature |
Nessus Agents; EPSS/VPR scoring; offline scanning support |
Greenbone Security Assistant; NASL scripting; complete source access |
Continuous monitoring; VR risk scoring; threat intelligence feeds |
| Learning Curve |
Easy |
Moderate |
Moderate-to-Steep |
Nessus Professional Keyboard Shortcuts
Keyboard shortcuts within Nessus web interface streamline vulnerability assessment workflows by reducing mouse navigation overhead. Web-based shortcuts enhance productivity during report review, scan configuration, and findings remediation tracking across distributed assessments.
| Action |
Windows/Linux |
macOS |
| Search in Interface |
Ctrl+F |
Cmd+F |
| Create New Scan |
Ctrl+N |
Cmd+N |
| Refresh Scan Results |
F5 or Ctrl+R |
Cmd+R |
| Export Report |
Ctrl+E |
Cmd+E |
Nessus Professional Performance Optimization
Optimizing Nessus Professional performance ensures rapid scan completion, efficient resource utilization, and maximum scanning throughput. Strategic configuration and tuning techniques eliminate bottlenecks and enable comprehensive assessments across large network environments within acceptable timeframes.
- Scan Threading Optimization – Increase ‘Number of Parallel Scanners’ to 16-32 for large networks to scan multiple hosts simultaneously; balance against network bandwidth to avoid saturation or false positives.
- Plugin Configuration – Disable unnecessary plugin families (printers, VoIP if not applicable) to reduce scan duration by 20-40% and improve relevance of findings to your environment.
- Database Maintenance – Run nessuscli system –config-optimization monthly to optimize Nessus database structure, improving query performance and UI responsiveness during large scan result reviews.
- Resource Allocation – Allocate minimum 8GB RAM; increase to 16GB for scanning 5,000+ hosts per scan. Monitor CPU usage; assign additional cores if sustained above 80% utilization during scans.
- Network Tuning – Adjust ‘Max Checks Per Host’ from default 5 to 2-4 for noisy networks prone to timeouts. Increase timeout values for WAN-connected systems experiencing latency.
Nessus Professional Accessibility Features
Nessus Professional provides comprehensive accessibility through web interface standards compliance, keyboard navigation support, and screen reader compatibility. Modern web technologies ensure accessibility for security professionals with diverse abilities requiring vulnerability assessment tools.
- Screen Reader Support – Web interface fully compatible with NVDA and JAWS screen readers; all scan results, plugin details, and reports announced correctly to assistive technology users.
- Visual Accessibility – High contrast mode available; adjustable font sizes through browser settings; color-blind friendly report visualizations with pattern differentiation beyond color coding.
- Keyboard Navigation – Complete keyboard-only operation without mouse requirement; all buttons, dropdowns, and functions accessible through standard web navigation and Tab key sequences.
- Language Support – Plugin metadata available in English (default), Japanese, Simplified Chinese, and Traditional Chinese; UI localization supports multiple international languages and RTL scripts.
Nessus Professional Support & Documentation
Nessus Professional includes comprehensive documentation, active community support, and optional commercial support plans. Multiple support channels ensure rapid resolution of technical issues and provide guidance for complex vulnerability assessment scenarios across diverse IT environments.
- Official Documentation – Comprehensive user guides at docs.tenable.com cover scanning, remediation, compliance auditing, and advanced features; updated with each release providing current feature documentation.
- Tenable Community Portal – Active community forum at community.tenable.com enables peer support, feature requests, and best practice discussions; Tenable support team monitors for critical issues.
- Video Resources – Tenable YouTube channel provides installation guides, scanning tutorials, compliance automation, and integration walkthroughs; community creators supplement official resources.
- Technical Support – Optional Advanced Support plan ($500/year) provides 24/7 phone support, dedicated support contacts, priority response times (P1 Critical: <2 hours, P4: <24 hours).