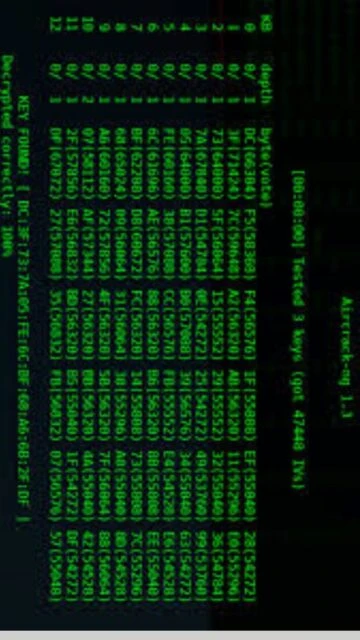
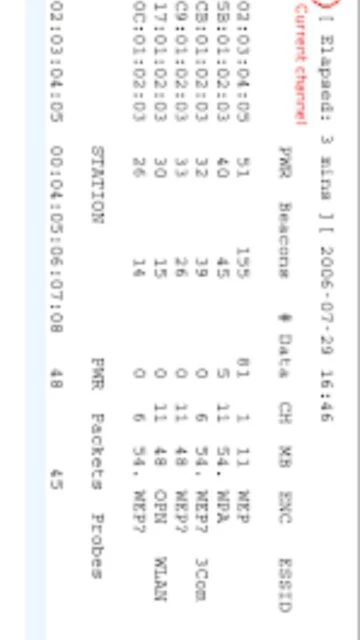
Aircrack-ng represents the industry-standard suite for wireless network security assessment and penetration testing. Originally forked from the Aircrack project in 2006 by Thomas D’Otreppe, this open-source collection delivers advanced capabilities for detecting, analyzing, and auditing wireless network security. Security professionals, network administrators, and ethical hackers rely on Aircrack-ng’s comprehensive toolset for evaluating WEP/WPA2 encryption strength, capturing handshakes, and performing sophisticated wireless attacks across Linux, Windows, and macOS platforms.
How to Install Aircrack-ng
Aircrack-ng installation varies significantly by platform. Linux users can leverage package managers for streamlined installation, while Windows users must manually extract pre-compiled binaries. Source compilation from GitHub provides the most up-to-date version across all platforms.
- Linux Installation via Package Manager – Run apt-get install aircrack-ng on Debian-based distributions or use your distribution’s native package manager for automated installation and dependency resolution
- Windows Binary Setup – Download the latest pre-compiled Windows archive from the official GitHub repository, extract contents to C:aircrack-ng-1.7-win directory maintaining the bin/src/test folder structure
- Compile from Source – Clone the GitHub repository, run autoreconf -i, execute ./configure –with-experimental, then compile using make and install with make install
- Verify Installation – Execute aircrack-ng –version to confirm successful installation and display the current version number and build information
Who Should Use Aircrack-ng
Aircrack-ng serves professional security practitioners conducting authorized wireless network assessments. Target users include penetration testers, security researchers, network administrators performing compliance audits, and participants in ethical hacking training programs.
- Penetration Testers – Conduct authorized WiFi security assessments for organizations evaluating their wireless infrastructure vulnerabilities
- Security Researchers – Analyze wireless protocols, test new attack vectors, and contribute to cryptographic security research and vulnerability documentation
- Network Administrators – Audit corporate wireless networks for security misconfigurations and assess employee network access compliance with security policies
- NOT ideal for – Unauthorized network access attempts, personal WiFi hacking without permission, or users lacking networking knowledge required for responsible tool usage
Aircrack-ng Platform Compatibility
Aircrack-ng maintains comprehensive cross-platform support through dedicated installers, package managers, and source compilation options. Each platform variant provides identical core functionality with platform-specific driver requirements and optimization enhancements.
| Platform |
Min. Version |
Unique Features |
Limitations |
| Linux |
Ubuntu 18.04+, Debian 10+ |
Full source compilation support, optimized performance with hwloc library, official Kali Linux preinstallation |
Requires ethtool, rfkill, and development tools; limited wireless adapter compatibility |
| Windows (Cygwin) |
Windows 7 SP1 or later |
Pre-compiled binaries available, GUI launcher included, .NET 4.6.1 required for graphical interface |
Limited wireless adapter support compared to Linux, requires Airpcap drivers for injection capabilities |
| macOS |
macOS 10.13 High Sierra+ |
Homebrew installation available, full feature compatibility, hardware acceleration support |
Wireless monitoring mode limitations on newer M-series chips, requires Xcode tools for compilation |
| BSD/Solaris |
FreeBSD 12.0+ |
Full source compilation, gmake compatibility, optimized with gcc9 for 50-70% performance boost |
Limited package manager support, compilation typically required |
Aircrack-ng Integrations & Plugins
Aircrack-ng integrates seamlessly with complementary security tools and frameworks through pcap file format compatibility and standardized data exports. These integrations enhance workflow efficiency for comprehensive wireless security assessments.
- Wireshark Integration – Export airodump-ng packet captures as pcap files for deep packet inspection and protocol analysis within Wireshark GUI
- Hashcat GPU Cracking – Convert Aircrack-ng handshake captures to Hashcat-compatible formats for accelerated password recovery using GPU computing power
- Metasploit Framework – Incorporate Aircrack-ng results into Metasploit wireless modules for automated exploitation and comprehensive penetration test documentation
- Kali Linux Suite – Comes pre-installed with full integration into Kali tools including AutoScan, Nexpose, and vulnerability management platforms for enterprise assessments
Best Alternatives to Aircrack-ng
While Aircrack-ng dominates wireless penetration testing, alternative tools offer specialized capabilities for specific assessment scenarios. Evaluate these options based on your testing requirements, hardware constraints, and expertise level.
- Kismet – Best for passive network discovery, provides comprehensive wireless device detection without active probing or network disruption
- Hashcat – Best for GPU-accelerated cracking, delivers dramatically faster password recovery using modern graphics card computing resources
- Wifite2 – Best for automated testing, simplifies Aircrack-ng complexity through automated tool orchestration and streamlined workflow automation
- WiFi Analyzer (Mobile) – Best for consumer WiFi optimization, analyzes signal strength and channel overlap for non-technical network improvement
Aircrack-ng vs Top Competitors
Comparing Aircrack-ng against competing wireless security tools reveals distinct strengths across different use cases. Each alternative addresses specific penetration testing scenarios with varying feature sets and performance characteristics.
| Feature |
Aircrack-ng |
Kismet |
Wifite2 |
| Pricing |
Free (Open-source) |
Free (Open-source) |
Free (Open-source) |
| Key Strength |
WEP/WPA2 cracking with PTW attacks |
Passive discovery without network disruption |
Fully automated testing workflow |
| Target Users |
Professional penetration testers |
Wireless network researchers |
Beginners and automated testing |
| Unique Feature |
40+ specialized tools in single suite |
Real-time network detection and GPS mapping |
Complete automated attack chains |
| Learning Curve |
Steep |
Moderate |
Easy |
Aircrack-ng Keyboard Shortcuts
Aircrack-ng command-line interface relies on parameter flags rather than traditional keyboard shortcuts. The suite provides extensive help documentation accessible through built-in help functions for each individual tool.
| Action |
Windows |
macOS |
| Display Help Information |
aircrack-ng –help |
aircrack-ng –help |
| Show Version Number |
aircrack-ng –version |
aircrack-ng –version |
| Start Monitor Mode |
airmon-ng start wlan0 |
airmon-ng start en0 |
| Capture Packets |
airodump-ng mon0 |
airodump-ng en1mon |
Aircrack-ng Performance Optimization
Maximizing Aircrack-ng performance requires proper hardware configuration, efficient capture file management, and strategic use of specialized attack algorithms. Advanced users implement parallel processing and GPU acceleration for dramatically improved cracking speeds.
- Enable Hardware Acceleration with hwloc – Compile with hwloc library support providing 50-70% performance improvement on high core-count processors and multi-socket systems
- Use PTW Attack Mode – Default Aircrack-ng implementation reduces packets needed from 700,000 to 35,000-40,000 for WEP key recovery, dramatically accelerating successful cracks
- Utilize GPU Acceleration via Hashcat – Convert Aircrack-ng captures to Hashcat format and leverage NVIDIA/AMD GPU computing for 100-1000x speed improvements in WPA2 cracking
- Configure Static SIMD Compilation – Compile with –with-static-simd specifying x86-avx2 or arm-neon for platform-specific optimization without generic code overhead
- Optimize Packet Capture Rate – Use airodump-ng –band ag –max-power to maximize packet capture efficiency and accelerate handshake collection
Aircrack-ng Accessibility Features
Aircrack-ng operates primarily through command-line interfaces with comprehensive text-based help documentation. The tool provides accessible information output suitable for terminal screen readers and alternate input methods.
- Screen Reader – Command-line output compatible with Windows Narrator and Linux screen readers through standard terminal text output
- Visual – Color-coded output in airodump-ng and other tools, high-contrast terminal display suitable for users with visual sensitivity or color blindness
- Motor – Full keyboard-based operation via command-line; no mouse input required for any tool functionality within the suite
- Languages – Documentation available in English with international community contributions; help text displays in system locale when available
Aircrack-ng Support & Documentation
Comprehensive documentation for Aircrack-ng spans official wikis, community forums, and video tutorials. Active development community on GitHub provides security updates and technical assistance for complex wireless testing scenarios.
- Official Documentation – Extensive wiki covering all tools, attack methods, platform-specific installation instructions, and troubleshooting guides for common issues
- GitHub Discussions – Recently migrated from traditional forums to GitHub Discussions for active community support, bug reporting, and feature requests
- Video Tutorials – Official YouTube channel and community-created guides demonstrating WiFi penetration testing workflows from basic to advanced techniques
- Contact Support – Direct GitHub issue reporting enables developers to track bugs, security vulnerabilities, and feature requests from the user community
 32
32